MalwareTech
OVERVIEW
MALWARETECH.COM TRAFFIC
Date Range
Date Range
Date Range
MALWARETECH.COM HISTORY
PERIOD
LINKS TO DOMAIN
Event logs with control characters. Indeed these control characters are included in at least 8 other events and all appear to be in date fields.
Wednesday, February 21, 2018. It is a process which runs in the background and mines for crypto-currency using your system as the resource. Disk utilization and CPU usage will be max. So your system will be slow. Application will take longer time to open.
Health Information Technology Rated a Top Patient Safety Issue. ONC Plans Data Sharing and Rx Guidance to Combat Opioid Over-Prescribing. Researchers unwrap app for improving mood and mental state. 25 Things to Know About Health IT Interoperability. The 2015 Edition Health IT Final Rule. At Lake Region, nurses carry the meaningful use message. CMS testing telehealth at nursing facilities.
Friday, January 8, 2016. Had reported the ZeroAccess infrastructure resumed distributing commands. Came across a previously unseen sample, which FireF0X.
Thoughts on malware and malware analysis. On May 16, 2017.
Análisis y pruebas de funcionamiento en exploits, malware y entornos inalámbricos. Análisis de Malware, se realizan pruebas de funcionamiento sobre los virus y troyanos más destacados.
Controlling BusyBox based routers with Metasploit. BusyBox, called the swiss army knife of embbeded linux, is a software application that combines tiny versions of common unix utilities into a single small executable, as we can read in the busyBox project page.
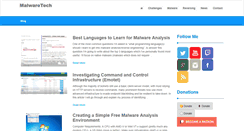
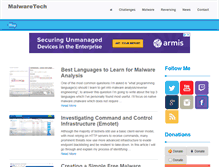
WHAT DOES MALWARETECH.COM LOOK LIKE?
CONTACTS
WHOISGUARD, INC.
WHOISGUARD PROTECTED
P.O. BOX 0823-03411
PANAMA, PANAMA, NA
PA
MALWARETECH.COM SERVER
NAME SERVERS
BROWSER IMAGE

SERVER OS
We identified that this website is utilizing the cloudflare operating system.HTML TITLE
MalwareTechDESCRIPTION
A detailed look into security and malware related topics from both an offensive and defensive point of view.PARSED CONTENT
The website malwaretech.com has the following in the web site, "Best Languages to Learn for Malware Analysis." We analyzed that the website also stated " One of the most common questions Im asked is what programming languages should I learn to get into malware analysisreverse engineering, to answer this question Im going to write about the top 3 languages which Ive personally found most useful." It also stated " Investigating Command and Control Infrastructure Emotet. Creating a Simple Free Malware Analysis Environment. Our sinkhole is designed t." The header had secuirty as the highest ranking search term. This keyword was followed by malware, rootkit, and botnet which isn't as urgent as secuirty. The other words they used was p2p. reverse engineering is also included but might not be seen by web crawlers.ANALYZE OTHER DOMAINS
A detailed look into security and malware related topics from both an offensive and defensive point of view. A collection of my security related code, including proof of concepts. A rootkit capable of surviving an operating system reinstall or disk reformat by infecting the hard disk firmware.
00 per Referrals to Jump-Start your Business. FREE to Start EARNING an Online Income. FREE Life-Time Multiple Income Portfolio. FREE Life-Time Multiple Traffic Portfolio. FREE Enrollments SPILLOVER into Your Downline. You can get Unlimited Website Traffic.
Malware Removal Assistance For Mobile. Malware Removal Assistance For Mac. Giveaways, Promotions and Contests. All the new laptops, All-in-Ones, and game-ready PCs Dell announced this week. Announcing Windows 10 Insider Preview Build 17639 for Skip Ahead.
Malware Tracker provides malware analysis, forensics, and security solutions for enterprise. Use Malware Tracker technology to detect malicious document attachments at the email gateway, and to automate the static analysis of PDF, and common document formats. Home of the free online PDF Examiner. The only web based PDF malware analysis suite and the Cryptam document malware scanner.
The List of Malware Types. Keep Passwords Safe in Business. Malware is Malicious Software, a Danger to Your Security. A new form of Malware is being created even as you are reading this post. There are many choices in protection you can make and many more you should not. Like driving a car, you should be able to get on your computer and drive it to your favorite website or email and just enjoy. The purpose of this site is to keep it that way for you.